Phishing Attacks In The Real World

When was the last time you almost lost $23,000 to a phishing email? This nearly happened to one of our clients this week. Fortunately, this phishing attempt was spotted before the funds were transferred, however, there are a few good lessons to take away from this story and we want to educate you so […]
Learn how to use a VPN
You may have heard of, or even used, a virtual private network (VPN), but do you know what it is? A VPN is an encrypted tunnel through a wide area network (WAN), also known as the Internet. This means that the network does not have to be located in one physical location, unlike a local area network (LAN). […]
Phishing For Passwords
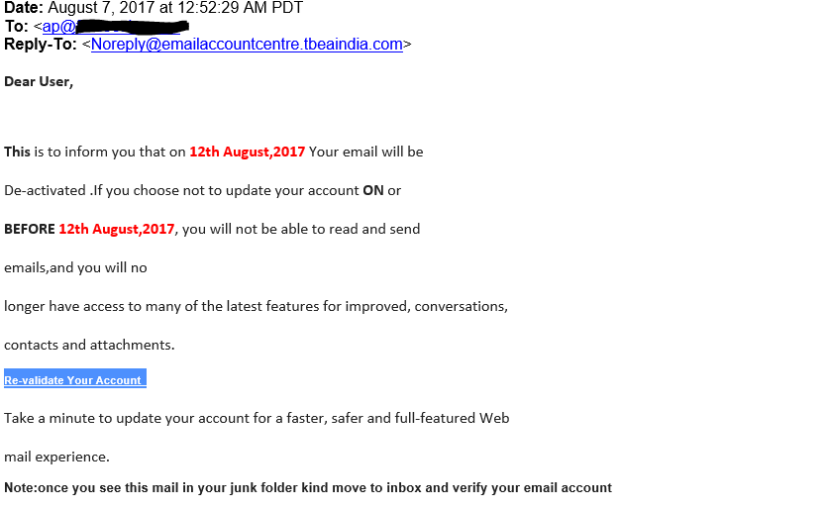
There has been a recent increase in phishing attempts across the US and it is concerning for many reasons. It is important to be aware of these issues and how these phishing attempts work so that you can protect yourself and your company. The unfortunate truth is that there is only so much you can do to […]
Use Technology To Avoid Pesky Salesmen

Technology has driven a wedge into the profession of sales in a way that industry wasn’t prepared to deal with. On the one hand, you rely on it to keep you connected, but on the other hand, you also want it to protect you and keep your life private as well. Salesmen look to utilize […]
PCI Compliance Audits
Have you ever been audited for PCI compliance? If not, it is most likely that at some point you will be. In order to maintain the ability to process payments electronically, this will be a fact of life. The more transactions you process in a year, the more often you will be getting a visit […]
How to prepare for ransomware
Lately, there has been a lot of talk about ransomware: a type of computer virus that encrypts your files and holds them for ransom. Worse yet, there is no guarantee that your data will be released if you pay the ransom fee. In light of the most recent ransomware attack called “WannaCry” that infected a substantial number of […]
Scam Email and Phishing Attempts
As an IT support company, we are always telling our friends and clients to be cautious with what they click on or whom they give personal information to. Most people know to avoid giving money to a Nigerian price, but scams and phishing attempts are becoming more advanced every day. Many scam emails disguise themselves as people […]
Business Information Technology Risk Assessment
In the spirit of St. Patricks Day, it is a good time to ask yourself how lucky you are. Since we are an IT consultant, we are going to focus on what that means when we look at an IT network. As an IT company, we get to see how a lot of businesses operate […]
The Growing Importance of Business Internet
Sooner rather then later, business IT networks will consist of an internet connection and a light weight computer that acts as a terminal to the internet. There will be no more investing in servers, switches, battery backups, NAS devices etc. in the same way that has been done for the last 15 years. Companies will […]
Popcorn Time Ransomware
While everyone is in the spirit of giving this holiday season, there is something to say about giving for the wrong reason. A new strand of ransomware is a good example of this. It’s called Popcorn Time. This new strand of ransomware will allow you two options if your computer is infected. You can choose […]




