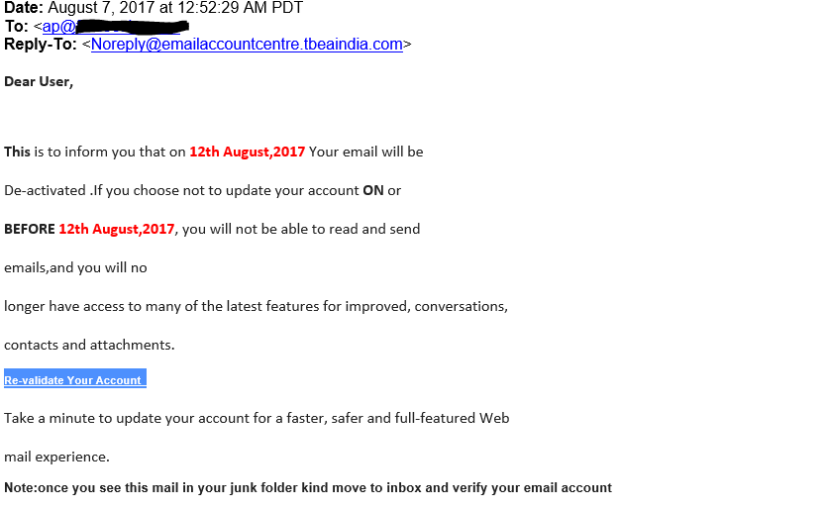
There has been a recent increase in phishing attempts across the US and it is concerning for many reasons. It is important to be aware of these issues and how these phishing attempts work so that you can protect yourself and your company. The unfortunate truth is that there is only so much you can do to block phishing emails from landing in your inbox in the first place. The only surefire way to prevent phishing attempts from becoming a problem is by training your users to keep a keen eye.
A phishing attack like the one shown above is an attempt to get you to give away some important information, usually credentials to an email account. In the past, phishing attempts have been highly generic like the “Nigerian Prince” scam that any most discerning individuals would understand to be malicious. Now that most people have become aware of the nature of phishing attempts, the scammers are having to become more sophisticated.
This means that phishing attempts will become increasingly difficult to distinguish from legitimate emails. As more and more emails are being hosted in the cloud through services like Gmail and Office 365, scammers have found a particularly effective way to trick people. These services will periodically ask you to verify your credentials or even change your password every 90 days. These routines can be hijacked to make you think that you are giving your information to your provider when really you are giving it to a scammer.
By looking at your publicly available DNS records, scammers can tell what email platform you are using. It is easy to set up a web page and design it to look exactly like the login page of any hosted email provider. Scammers will use this information to send you highly targeted emails asking you to verify your credentials for “security” reasons. Seeing that the email appears to be from a trusted source, and the link in the email supposedly leads to your hosted email provider, you are likely to enter your password giving the scammer access to all of your information.
In order to help you avoid these pitfalls, we have a few simple steps to follow that will help keep you safe.
- Are you expecting the email? Maybe you are logging in from a new computer and the email host doesn’t recognize or trust your device. This is a good reason to expect an email with a link. If there is no reason to expect an email, then receiving one should be a red flag.
- Inspect the email. Start by looking at the sender. Do you know them? Don’t just look at the display name; carefully inspect the email address that the email is coming from. Is the domain address spelled correctly? If not, this is likely a scam. Does the email use scary works like Urgent or Emergency? This should be a red flag as well. Also, be sure to check any external link addresses and if they lead to an obscure website, this is likely a scam.
- Don’t use links. If you have reason to think that this email is legitimate, take one last security precaution and don’t use the link provided. If you need to verify your credentials then you will be prompted to do so the next time you log into your email account. Do a web search for the login page of your hosted email provider and log into your account from there. If you are not prompted to verify your login then you will know that the email you received is a scam. If it is a link from a known sender, you could also give them a call to verify that the link is from them.
Following these steps will allow you to filter out most phishing attempts that make it to your inbox no matter how sophisticated they become. These attacks rely on you making decisions while not fully paying attention, but they will never be able to fully copy the email provider they are trying to spoof. This means that if the email is not legitimate, then you will likely be able to point that out with a few seconds of careful inspection.
As always, be sure to work closely with your IT professional to ensure that you have a security plan in place. Phishing attempts can lead to data loss, security breaches and even significant lost revenue. It is always better to be preventative about these issues than having to deal with the aftermath.